It is scary to think that 97% of people around the globe cannot identify a sophisticated phishing email1. An online phishing attack involves using electronic communications to take advantage of you, by tricking you into giving away personal data such as login credentials and credit card numbers. While these attacks have been around for a long time, being able to spot them has become increasingly difficult as they increase in complexity. With the number of targeted phishing attacks on the rise, and spam filters not always effectively diverting these unwanted emails to junk, it is critical for you and everyone in your organisation to know how to spot one. This is an imperative part of your organisation’s digital security. No matter how hardened your IT security measures are, your users will always remain the weakest link in the security chain.2 Take note and share these 7 important ways to avoid phishing attacks within your business:
1. Always check the sender’s address and domain name
Don’t just rely on the sender’s name. It is easy for phishers to set their display name so you think it is from a trusted source. Realistically, checking the actual email address should give you a major clue as to if the sender is legitimate. For example, the display name could be your banking institution’s name, but the domain from the sender’s email address will not match. Another trick that phishers try with domain names is spelling them very similarly to what they should be, so make sure you examine the domain name carefully.

2. Check spelling and grammar
Legitimate companies will always spell all correspondence accurately, in fluent English and using correct grammar. Pay close attention to any spelling mistakes or grammatical errors that native speakers would not normally make. This could be a sign the correspondence is not genuine.
3. Don’t open suspicious attachments
Unless you are certain the attachment is from a legitimate party, you should never open it. It could download malware to your device and perform any number of nefarious activities, including viruses. If you are uncertain about the attachment and the email address appears to be legitimate from a sender you know, then simply reply to them asking about the attachment and how it is best opened. Most people won’t mind confirming.
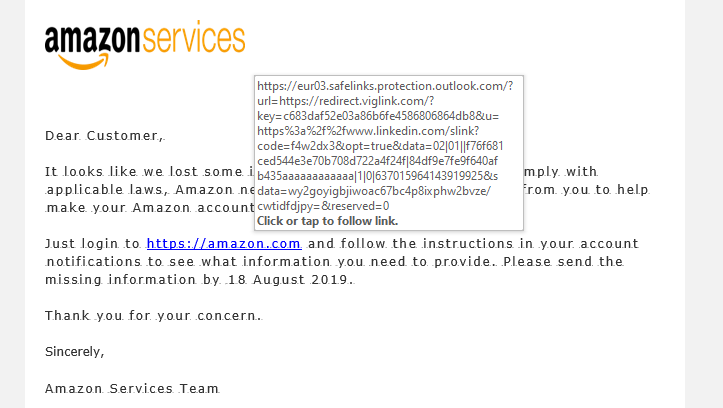
4. Don’t click suspicious links
Ensure the destination of the link matches the context of the rest of the correspondence. Always check where the link is going to. This can be done by hovering over the link and checking the address, or on phones by holding down the link to see a pop-up of the address.
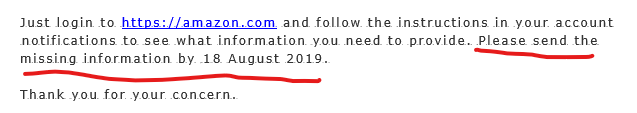
5. Does the correspondence create a sense of urgency?
Often phishing attempts will have a sense of urgency around them to try to get you to act quickly and put pressure on you. This can be a red flag. Some phishers are even sophisticated enough to create an email that is seemingly from your boss or superior, asking you to hurriedly put through an invoice or sign up to a website. This urgency may cause you to overlook unusual aspects of the email and may even make you too uncomfortable to ask your boss about it. However, it is always better to be safe rather than sorry. So if you are receiving an email from someone you seemingly know, especially if they are asking for money, it’s always best to check with them first.
6. Pay attention to the greeting
Safe emails will almost always address you by your name. It can be a clue that the correspondence is ingenuine when they refer to you in generic ways such as “valued customer” or simply “sir/madam”. Best practice is always to merge a customer’s personal information into an email nowadays, so when the sender only has generic information about you, it could be a phishing attack.
7. Review the signature
Make sure the email signature has an alternate method of contact, as all legitimate businesses will include this, as well as an unsubscribe option. If you are ever unsure about the content in a message you can always try contacting them via these alternate methods. If they do not provide one, it can strongly suggest a phishing attack.

Overall, you should be wary of any email that asks for personal information. Apply these principles and ensure you and your organisation stay safe and protected from phishing attacks. Most legitimate companies make the promise that they will never ask you for personal information via an email. So, if you find your bank or trusted online shopping provider requesting you login after clicking an email link, or asking you to confirm your contact details, it is better to err on the side of caution and think twice. It is important to ensure that, not only you, but everyone in your organisation is savvy when it comes to these important tips and tricks. It only takes one vulnerability to be breached for important data to be shared with unwanted parties. Follow the above suggestions and you should be able to avoid these unwanted phishing attacks and keep your personal and business data safe.
Share this article with a colleague (with the button at the top of the page) to help them avoid phishing attacks.
By Isabella Mitchell
1 https://blog.returnpath.com/10-tips-on-how-to-identify-a-phishing-or-spoofing-email-v2/
