By Gavin van Niekerk, CyberSecurity Practice Lead, Quorum
As Satya said “We have seen two years’ worth of digital transformation in two months.”
I have been very fortunate in my career to work with excellent teams and attend a number of Microsoft events, forums, and courses. I can say I am not easily impressed. Well, I guess “I am not easily surprised” is more accurate. Microsoft Inspire was excellent and I cannot thank all those involved enough; I was truly in awe! The energy that the Microsoft crew brought to Inspire in these extremely challenging times was fantastic. Well done!
So… I am a technologist, security nut, it does go on (but we have a limited word count). I went into Inspire with a mindset that I would purposely watch sessions that I had no clue about, or those which I thought would challenge my thinking.
The following are the sessions that stood out for me.
Mitra Azizirad’s session ~ Envisioning Tomorrow: How Microsoft approaches innovation


The future is discovered when we see things from a different perspective.
AI is a fascinating science (with a bit of creative art thrown in – love this picture) which I think will hold a lot of potential when it comes to solving practical as well as complex challenges, we are likely to face in “our new normal”.
Brad Anderson’s session Microsoft Endpoint Manager: Productivity from any device, anywhere.


Brad is just such a cool guy (somewhere between Bruce Willis and Lone Survivor <2013 movie>); I also love his green-screen videos. His session on Microsoft Endpoint Manager was extremely pertinent as it can – and has – solved several “remote work” issues that organisations have been thrust into. It reminded me of doing more with less and how things may change as we adapt going forward.
After a good round of non-security and compliance sessions, I could not help myself and joined some, these included:
Help customers reduce risk and build resilience with security, compliance and identity solutions
Build profitable managed security services with Azure Sentinel and Microsoft Threat Protection
The following session on Zero Trust was excellent, especially as, while I believe the term is known, many are not clear on exactly what it is, what it includes, excludes, etc.
Zero Trust starts with a strong identity foundation.
We know that Identity is the new security boundary (if you didn’t, you do now!), and a key pillar within the Zero Trust strategy. <first clue> It is a strategy.

Sue Bohn outlined Zero Trust like this: the era of remote work demands a new security approach – one that explicitly verifies every authentication request and implements an ‘assume breach’ posture. A strong identity foundation is essential to secure remote access and helps customers start their Zero Trust journey.
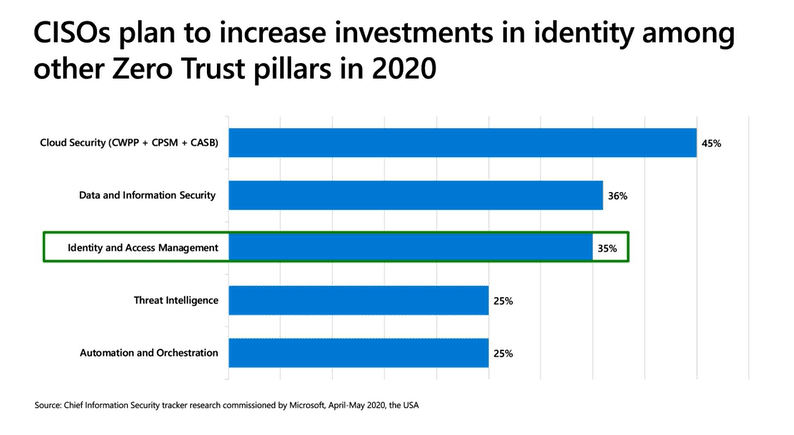

Azure Active Directory is a multi-functional Identity and Access Management platform, but it is also a key component of our Zero Trust strategy. How is that? We require a robust, scalable and secure platform that can be used to “evaluate” every authentication and authorization from a risk perspective <second clue>.
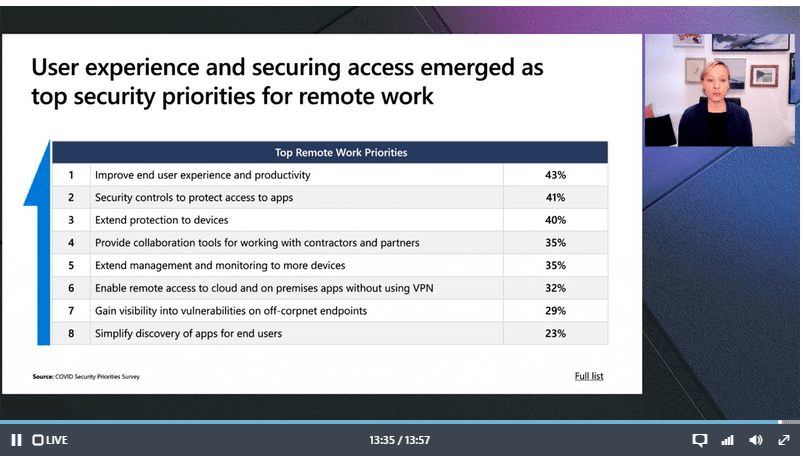

Security (and Zero Trust) still need to strike a balance <third clue> between user experience, productivity and control. This continues to be a top business priority and cannot (well should not) be ignored.
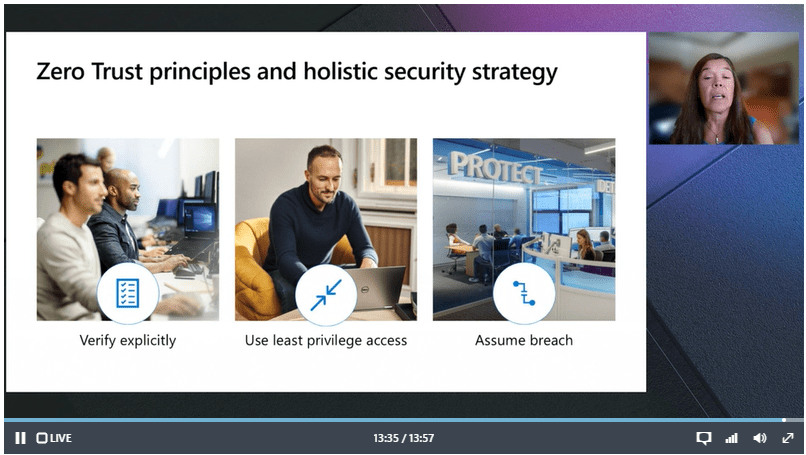

Now that we have a solid foundation there are a couple of other components required for our strategy:
- Verify explicitly – Done via Azure AD
- Use least privilege access – Done via Azure AD
- Assume breach – Consistency here is key; we need effective insights across Identity, Endpoints, Apps and Data.
We can take a slightly different view of the architecture like this:
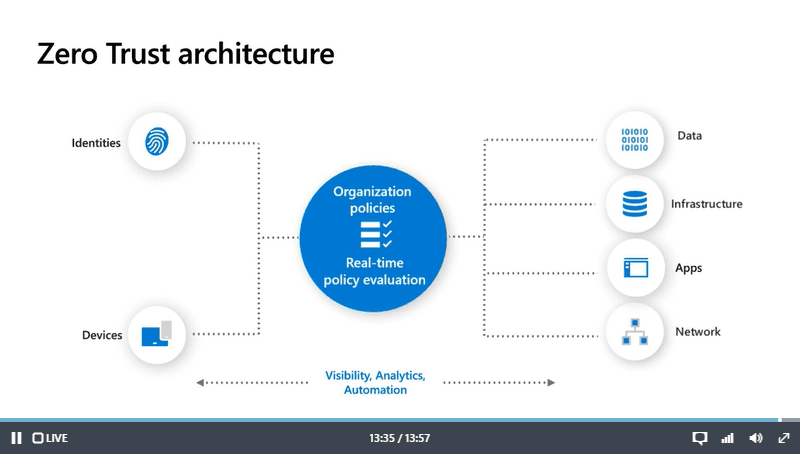

While every organization is different and each journey will be unique, a Zero Trust security model is most effective when integrated across the entire digital estate, most organizations will need to take a phased approach that targets specific areas for change based on their Zero Trust maturity, available resources, and priorities.
The Zero Trust assessment is an excellent starting point as you define your own strategy, also remember the <clues>:
- Identity is the new security boundary
- Zero Trust is a strategy
- Strike a balance between appropriate risk and control
I started with Satya, and I’ll end with Satya. He once said, “cybersecurity is like going to the gym. You can’t get better by watching others, you’ve get to get there every day.”

Just as Satya is saying with his gym analogy that we need to do the work, I’m also saying that we need to do the work. In working out how Zero Trust will be a strategy in your organisation, along with Identity being the new boundary, you will find that balance that works best for your needs.
Just as I had several take-aways from Microsoft Inspire, I hope that you to will be Inspired as we continue our digital journey through security and compliance.

